This blog post aims to explore the broad field of questionable practices and map the terrain, so to speak, that we are traversing in regards to the phenomenon of predatory publishing. First, we will discuss essential characteristics and concepts related to the phenomenon of predatory publishing. The second part of the paper explores the various catchwords we find in discussions about the field of predatory publishing. We explain and compare these catchwords in an effort to elicit a clearer picture of the many different variants within the broader field of predatory publishing.
When capturing questionable practices in scholarly communication, the term predatory publishing is quickly and easily at hand. However, arriving at a concise definition is not so trivial. Upon closer examination, it soon becomes evident that the term predatory publishing covers a wide array of dubious practices. To illustrate, when analyzing journals, the database Cabells Predatory Reports appliesmore than 70 indicators.
Predatory publishing is not limited to ruthless practices regarding scientific journals as it also affects collected works and conference proceedings. There may be entire publishing houses pursuing a fraudulent business model. Other questionable practices in scholarly communication may also stem from authors. In cases of scientific misconduct or even fraud, research articles are published preferably in predatory journals (Ginther 2019). As there are deficiencies in the peer review process, if a review is conducted at all, the research findings appear legitimate throughout publication as part of a (supposedly) scientific journal. These outlets, in turn, become a medium to support inferior quality research, yet, at the same time, high-quality research can be published in an inferior publication medium. In order to do justice to this complex matter, it would be more appropriate to use the broader terms such as predatory practices or questionable practices, rather than just talk about predatory publishing unless, of course, one is addressing a specific practice and chooses the corresponding term.
A single, comprehensive definition of the term predatory practices is a difficult undertaking. The field is far too complex to simply divide them into ‘good’ or ‘bad’ categories. Cabells’ journal directories, for example, were originally named blacklist and whitelist. In 2020, blacklist was changed to Predatory Reports and whitelist is now Journalytics. In doing so, Cabells has distanced itself from discriminatory language. In our opinion, however, the new wording also mitigates the rigid division into good and bad.
Agnes Grudniewicz’ et al. (2019) much cited definitionfor Predatory Practices/Predatory Publishing refers to journals and publishers:
Predatory journals and publishers are entities that prioritize self-interest at the expense of scholarship and are characterized by false or misleading information, deviation from best editorial and publication practices, a lack of transparency, and/or the use of aggressive and indiscriminate solicitation practices.
One reaction to this definition was to address the missing reference to the fundamental importance of peer review (Dobusch et al. 2020). Grudniewicz et al. point out in their article that reputable journals, by keeping their peer review practices under lock and key, abet “predatory” practices, however, their definition lacks an essential reference to the quality of peer review. If some form of open peer review were standard, journals publishing non-peer-reviewed articles would quickly be revealed.
When analyzing journals, it may seem easier to look at what qualifies high quality academic journals and assess characterizing features instead of searching for unsound practices. Unfortunately, we quickly reach our limit as fraudulent journals generally pretend to be transparent in all/many aspects of the publication process but they are, in fact, making false claims in order to deceive potential authors, readers, or others. For example, as previously mentioned, peer review does not exist. Other examples of deception would be to present a fictitious editorial board, or choose a journal title that sounds very similar to that of a legitimate journal, among others. However, it is important to bear in mind that there are also other renowned journals that at times do not adhere to high standards of quality and/or are less transparent or deficient in regard to quality standards. However, in these cases, there is (usually) no intent to commit fraud and applying the term predatory journal to these journals is unwarranted. In this case, one option might be to apply the term low-quality journals. Separating low-quality journals that have a actual scientific claim from those that have fraudulent agendas is important. Some of the former are new open access journals that have yet to establish themselves (Ginther 2019). In this regard, critically evaluating the details is pivotal, along with examining the information about a journal. Overall, it can be said that deliberate deception – such as services offered and paid for but not delivered – separates the chaff from the wheat. Ascertaining intent, however, is easier said than done. Given this context, the spectrum approach, introduced by the Inter Academy Partnership (IAP) in their recent report Combatting Predatory Journals and Conferences, is a valuable and useful approach when categorizing scientific journals and conferences. In terms of quality, their seminal concept to locate journals on a sliding scale is also consistent with our understanding and approach when identifying predatory practices. The IAP spectrum covers seven types of journals spanning from recognizably fraudulent to quality journals: (1) fraudulent journals, (2) deceptive journals, (3) unacceptable low-quality journals, (4) low quality journals, (5) promising low quality journals, (6) questionable quality journals, (7) quality journals. The scale is, similar to a traffic light, split into three sections ranging from high risk to low risk. The seven types of journals are placed within this range and IAP provides pertinent characteristics for each type. The grading process requires an in-depth examination of a journal’s website as well as its context. Editorial board members, for example, are more closely scrutinized and any information regarding various metrics must be verified. The analysis and the characteristics as outlined in the seven-tiered scale ultimately provides a more comprehensive understanding of a journal, thereby assisting authors and other interested parties when deciding on a journal’s legitimacy and quality.
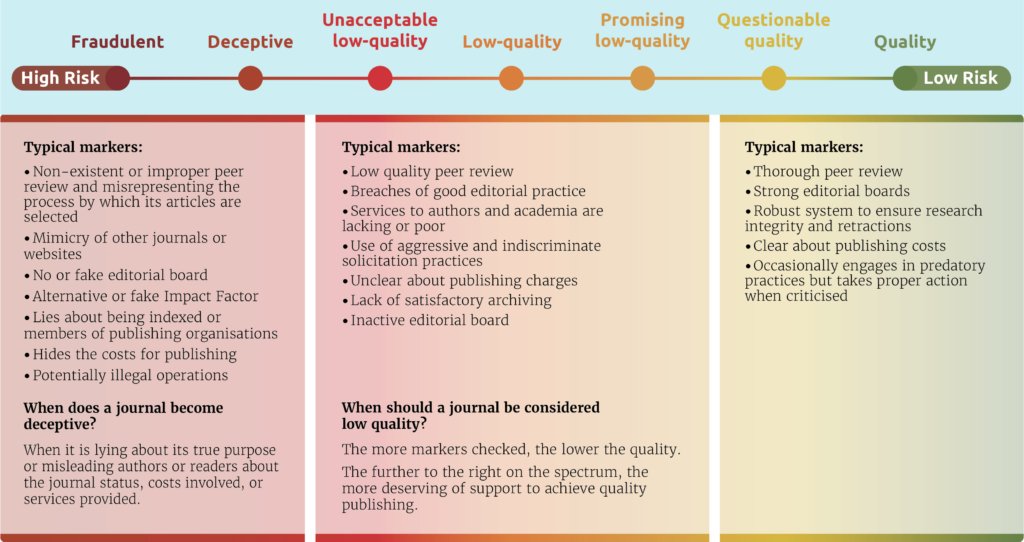
The so-called ‘author-pays model’ is an open-access funding model that protagonists in predatory publishing take particular advantage of. Reputable Gold OA journals use the money obtained through Article Processing Charges (APCs) to finance editorial services, layout, marketing, etc. Predatory journals aim to benefit themselves financially and shamelessly exploit this type of funding model by charging these fees but failing – or very inadequately providing – the promised services. The result is mainly public funds falling into the hands of “fraudulent” parties.
There are many other cases related to Predatory and Other Phenomena in Academia in which something similar is happening. The circulating terms shall now be briefly explained and, in order to facilitate a basis for discussion, will be put into context. On account of various influencing factors, we face an increasing level of questionable – or quite simply false – information, content (fake news), and practices. Unfortunately, these fakes (sometimes also referred to as scams) do not just affect scholarly communications, we also find them in the form of fake publishers, fake journals, fake papers, fake peer review, and fake conferences. The collective term fake science is also frequently used in this context, though we should be careful to not confuse this term with junk science, a term often used by various interest groups to discredit unwanted research results. As mentioned above, while the promised intention to support scientific progress and maintain research integrity masquerades as adhering to established scientific and academic standards, it is only sporadic or anything but. Coupling this with the goal financial gain from publication or participation fees, then we are talking about a predatory publisher, a predatory journal, or a predatory conference. Other often used terminology in this context include questionable (or suspicious) journals and conferences. These are not necessarily fake or even predatory; they may simply be publications or conferences of inferior quality. As a result, conferences can also be assessed in a different way by applying the IAP’s spectrum approach (see figure 2).
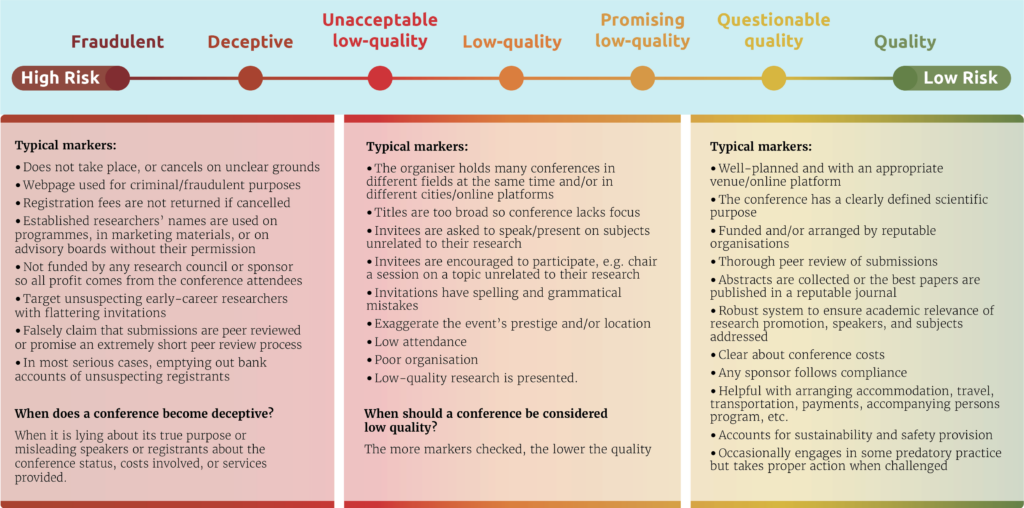
On the left side of the publication spectrum, one of the most worrying phenomena are the so-called paper mills. These are shady, profit-oriented companies where ready-to-submit scientific papers (including the “acquisition” of authorship) can be ordered by paying a fairly considerable fee. Whereas up to now we only addressed more or less questionable practices, this type of true academic ghostwriting crosses the line into scientific misconduct or fraud. This may be potentially exacerbated by the fact that the “written” manuscripts (which are often only assembled from other publications) have been plagiarized, or the research findings are based on falsified, or even stolen, data (cf. e.g. Bik 2020, Else & Van Noorden 2021).
One of the more recent “achievements” in the predatory publishing universe are so-called bootlegged or rebranded papers. In 2021, during the course of initial analyses of data collected as part of the Lacuna project (lacunadb.io)*, Siler et al. discovered that, for example, the branding of certain OMICS journals had been removed and they were still being published (using the same ISSNs and DOI prefixes). Furthermore, it was discovered that certain dubious journals were re-publishing articles that had already been peer-reviewed and published elsewhere. Lacuna’s long-term goal is to build a database of publishers and journals not listed in standard bibliographic databases, such as Web of Science or Scopus. As in the case of IPA, a spectrum approach will be followed with regard to their categorization (from “malicious fakes to scrappy, under-resourced start-ups”).
*At the time of this blog post’s publishing, the website is no longer accessible.
When dubious sources are cited or referenced as part of scientific publications, this is referred to as citation pollution or contamination. These may be publications whose authors who cite themselves (e.g. Van Noorden & Chawla 2019, Chakraborty et al. 2022), but also articles published in predatory journals. At this point we should note that this type of questionable literature can also originate from a reputable source, for example, articles that originally appeared in a renowned journal and were then retracted after publication on account various reasons (e.g., scientific misconduct or even fraud). A recently published paper by Jeffrey Brainard reporting the results of an Avenell et al. study published in June 2022 introduced the term zombie papers. They are “undead” because even though they have been retracted, they “live on” thanks to their citations.
In 2010, Ivan Oransky and Adam Marcus launched Retraction Watch (https://retractionwatch.com) to raise awareness and improve transparency in this area. Originally initiated as a blog to address the retraction of scientific publications and various related topics, this initiative also manages a very important and comprehensive database, the Retraction Watch Database (https://retractiondatabase.org). The corresponding Zotero integration (https://www.zotero.org/blog/retracted-item-notifications) can help authors identify these kinds of retracted papers more easily in their own bibliography or references.
Another very useful tool created as part of this initiative is the Retraction Watch Hijacked Journal Checker (https://retractionwatch.com/the-retraction-watch-hijacked-journal-checker), an online index compiled by Anna Abalkina (Free University of Berlin) and last updated on June 15, 2022, currently listing 153 titles (also see Else 2022). Hijacked journals are journals that imitate reputable journals by fraudulently taking over their titles, ISSNs, etc. These journals, sometimes also referred to as cloned journals, often advertise an accelerated publication process and often make false claims, such as indexing in renowned scientific databases, in order to mislead academics and lure them into submitting their articles. As predatory practices are elaborate and multifaceted, raising awareness among those who actively take part in the academic publishing process – be it authors, administrative staff at universities and librarians – is vital, especially when providing information regarding core competencies related to publishing one’s scholarly record. Those offering services pertaining to scholarly communications have a clear mandate yet, this alone is insufficient when it comes to staving off questionable practices and parties. Additional initiatives are needed to increase transparency during the publishing process and keep impostors at bay.
References
Avenell, A. et al. (2022). A randomized trial alerting authors, with or without coauthors or editors, that research they cited in systematic reviews and guidelines has been retracted. Accountability in Research. https://doi.org/10.1080/08989621.2022.2082290
Bik, E. (2020). The Tadpole Paper Mill. Science Integrity Digest (21 February). https://scienceintegritydigest.com/2020/02/21/the-tadpole-paper-mill
Brainard, J. (2022). ‘Zombie papers’ just won’t die. Retracted papers by notorious fraudster still cited years later. Science 377 (6601), 11-12. https://doi.org/10.1126/science.add6848
Chakraborty, J.; Pradhan, D. K.; Nandi, S. (2022). Research Misconduct and Citation Gaming: A Critical Review on Characterization and Recent Trends of Research Manipulation. In: Sharma, N.; Chakrabarti, A.; Balas, V. E.; Bruckstein, A. M. (eds). Data Management, Analytics and Innovation. (Lecture Notes on Data Engineering and Communications Technologies 71). Springer, Singapore. https://doi.org/10.1007/978-981-16-2937-2_30
Dobusch, L. et al. (2020). Predatory journals: tell-tale lax review. Nature 580/7801, 29. https://doi.org/10.1038/d41586-020-00911-x
Else, H. (2022). Hijacked-journal tracker helps researchers to spot scam websites. https://doi.org/10.1038/d41586-022-01666-3
Else, H. & Van Noorden, R. (2021). The fight against fake-paper factories that churn out sham science. Nature 591, 516-519. https://doi.org/10.1038/d41586-021-00733-5
Ginther, C., & Lackner, K. (2019). Predatory Publishing – Herausforderung für Wissenschaftler/innen und Bibliotheken. O-Bib. Das Offene Bibliotheksjournal / Herausgeber VDB, 6(2), 17–32. https://doi.org/10.5282/o-bib/2019H2S17-32
Grudniewicz, A. et al. (2019). Predatory journals: no definition, no defence, Nature 576, 210-212. https://doi.org/10.1038/d41586-019-03759-y
Linacre, S. (2020). Predatory publishing from A to Z. Cabells (12 February). https://blog.cabells.com/category/blacklist-criteria
Siler, K. et al. (2021). Predatory publishers latest scam: bootlegged and rebranded papers. Nature 598, 563-565. https://doi.org/10.1038/d41586-021-02906-8
The InterAcademy Partnership (IAP) (2022). Combatting Predatory Academic Journals and Conferences (Full Report in English). https://www.interacademies.org/publication/predatory-practices-report-English
University of Cambridge, Office for Scholarly Communication: Predatory Publishers. https://osc.cam.ac.uk/about-scholarly-communication/author-tools/considerations-when-choosing-journal/predatory-publishers
Van Noorden, R. & Chawla, D. S. (2019). Hundreds of extreme self-citing scientists revealed in new database. Nature 572, 578-579. https://doi.org/10.1038/d41586-019-02479-7
Ware, M.; Mabe, M. (2015): The STM Report: An overview of scientific and scholarly journal publishing, The STM Report, 4th ed., Oxford: International Association of Scientific, Technical and Medical Publishers. https://digitalcommons.unl.edu/scholcom/9


Leave a Reply